Certifications
Be Confident, not Constrained
Total Expert is committed to flawless data security. We deploy best-in-class technologies and processes to safeguard all your information—whether it’s in transit, in use, or at rest.
Security Tools
Tested, trusted data security
Audit trails
We use automated auditing tools to track precisely who accesses your data, when it’s accessed, which automated processes are acting on your data, and when your data is updated. In addition to providing you with control and visibility, these audit trails help simplify compliance.
TCPA and CAN-SPAM
Email and text (SMS) are staples in most marketing programs. But while they’re convenient, they also carry potential compliance risks. Total Expert’s email and texting systems feature automated workflows for approvals, reporting, and auditing so your messages are sent using the industry-standards for compliance.
Staying compliant with the CCPA
Total Expert is an approved service provider of the California Consumer Privacy Act (CCPA). We process personal information only on behalf of our customers, pursuant to written contracts. Those contracts, which are already in place, permit Total Expert to process our customers’ data only for the purpose of providing our services. While we process personal information through our network, we never sell that information to third parties.
Our security approach
Our approach to security is informed heavily by the NIST Cybersecurity Framework, AWS Well-Architected Framework, and other relevant and widely recognized industry standards. In addition, Total Expert is American Institute of CPAs (AICPA) SOC2 compliant, which means the design and operating effectiveness of our controls meet their rigorous standards.

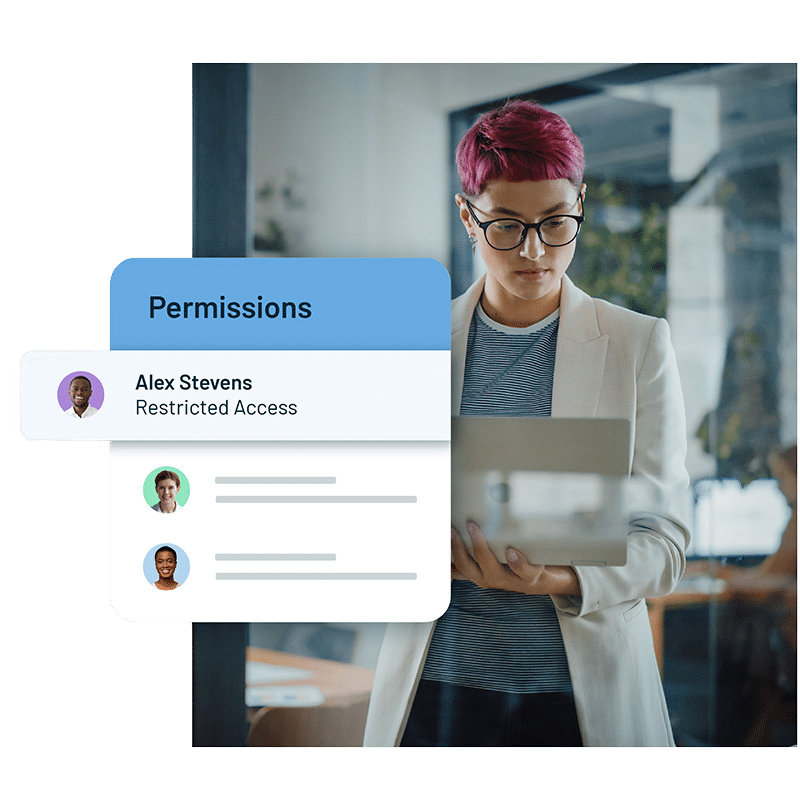
Complete control over data access
Leverage your single sign-on (SSO) provider to enforce enterprise-specific policies and simplify the login process for your users, while maintaining the additional security of multi-factor authentication (MFA). These identity systems allow you to manage precise privileges and control access to your organizational data, so users are only given the access they need to do their job.
Continuous monitoring of authorized sessions
We leverage adaptive authentication technologies to ensure the identity of authorized users. This includes key security considerations like device reputation, user location, IP address, and user behavior. We also monitor every session to make sure users only access data that matches their privileges—and to ensure sessions aren’t hijacked via man-in-the-middle attacks.

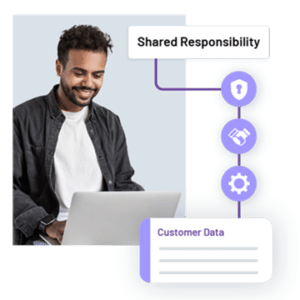
Shared responsibility model
Total Expert provides you with the tools and support you need to ensure that all users engage in appropriate and compliant use of our platform. As a customer, you have everything you need to coach users and ensure they are protecting customer data in your day-to-day operations. Total Expert and its technology partners assume full responsibility for the security of the platform itself. This Shared Responsibility model is built on best practices refined over years of deployment.
Beyond digital: 24/7 physical security
Total Expert partners with Amazon Web Services (AWS) as our infrastructure provider. This means your data is hosted in U.S.-based data centers that feature 24/7 physical security. These data centers are protected with best-in-class security systems that carry SOC2 and ISO certifications—so your data is just as safe on the ground as it is in the cloud.


See it in action
We know that seeing is believing. Let us show you the power of Total Expert.
Knowledge & insights
Stay up to date with the latest financial news, industry trends, and Total Expert tips.